Featured
Table of Contents
How To Get Started With Wireguard Vpn
It is currently under heavy development, however already it may be considered the most secure, easiest to utilize, and most basic VPN option in the industry. Wire, Guard intends to be as easy to configure and release as SSH. A VPN connection is made just by exchanging very basic public secrets precisely like exchanging SSH keys and all the rest is transparently managed by Wire, Guard.
Wire, Guard presents an incredibly fundamental yet effective interface. Wire, Guard has been developed with ease-of-implementation and simpleness in mind.
You then might progress to setup and reading the quickstart directions on how to use it. If you have an interest in the internal inner functions, you might be thinking about the short summary of the procedure, or go more in depth by reading the technical whitepaper, which goes into more detail on the procedure, cryptography, and basics.

This interface acts as a tunnel interface. Wire, Guard associates tunnel IP addresses with public secrets and remote endpoints. When the user interface sends out a package to a peer, it does the following: This packet is implied for 192. 168.30. 8. Which peer is that? Let me look ... Okay, it's for peer ABCDEFGH.
Should Businesses Consider Wireguard?
If not, drop it. Behind the scenes there is much occurring to provide appropriate personal privacy, authenticity, and ideal forward secrecy, using modern cryptography. At the heart of Wire, Guard is an idea called Cryptokey Routing, which works by associating public keys with a list of tunnel IP addresses that are permitted inside the tunnel (what is wireguard protocol and how does it work?).

Each peer has a public key. Public keys are short and easy, and are utilized by peers to authenticate each other. They can be passed around for usage in setup files by any out-of-band method, comparable to how one may send their SSH public key to a good friend for access to a shell server.
69:51820 Allowed, IPs = 0. 0.0. 0/0 In the server setup, each peer (a client) will be able to send packages to the network user interface with a source IP matching his matching list of permitted IPs. For example, when a package is received by the server from peer g, N65Bk, IK ..., after being decrypted and authenticated, if its source IP is 10.
230, then it's enabled onto the user interface; otherwise it's dropped. In the server setup, when the network interface wishes to send a package to a peer (a client), it looks at that package's destination IP and compares it to each peer's list of enabled IPs to see which peer to send it to - what is wireguard protocol and how does it work?.
Wireguard — A Closer Look

10.10. 230, it will secure it utilizing the general public secret of peer g, N65Bk, IK ..., and then send it to that peer's latest Web endpoint. In the customer setup, its single peer (the server) will be able to send out packets to the network interface with any source IP (because 0.
0/0 is a wildcard). When a packet is gotten from peer HIgo9x, Nz ..., if it decrypts and authenticates properly, with any source IP, then it's permitted onto the interface; otherwise it's dropped. In the client configuration, when the network interface wishes to send out a package to its single peer (the server), it will secure packages for the single peer with any destination IP address (given that 0.
0/0 is a wildcard). For instance, if the network interface is asked to send out a packet with any destination IP, it will secure it using the general public key of the single peer HIgo9x, Nz ..., and after that send it to the single peer's newest Internet endpoint. In other words, when sending out packages, the list of permitted IPs acts as a sort of routing table, and when receiving packets, the list of allowed IPs acts as a sort of access control list.
Any combination of IPv4 and IPv6 can be used, for any of the fields. Wire, Guard is fully efficient in encapsulating one inside the other if required. Because all packets sent on the Wire, Guard user interface are secured and confirmed, and because there is such a tight coupling between the identity of a peer and the permitted IP address of a peer, system administrators do not need complex firewall program extensions, such as in the case of IPsec, however rather they can simply match on "is it from this IP? on this user interface?", and be assured that it is a safe and authentic packet.
Vpn Protocols - What They Are And The Differences ...
The client setup consists of an initial endpoint of its single peer (the server), so that it understands where to send encrypted information prior to it has actually gotten encrypted information. The server configuration doesn't have any preliminary endpoints of its peers (the customers). This is since the server discovers the endpoint of its peers by examining from where properly confirmed data stems.
If you're having trouble establishing Wire, Guard or using it, the very best place to get help is the #wireguard IRC channel on Libera. Chat. We also go over development tasks there and plan the future of the job. Get involved in the Wire, Guard advancement discussion by joining the subscriber list.
Do not send out non-security-related issues to this e-mail alias. Do not send security-related concerns to various e-mail addresses. The kernel parts are released under the GPLv2, as is the Linux kernel itself. Other jobs are accredited under MIT, BSD, Apache 2. 0, or GPL, depending upon context.
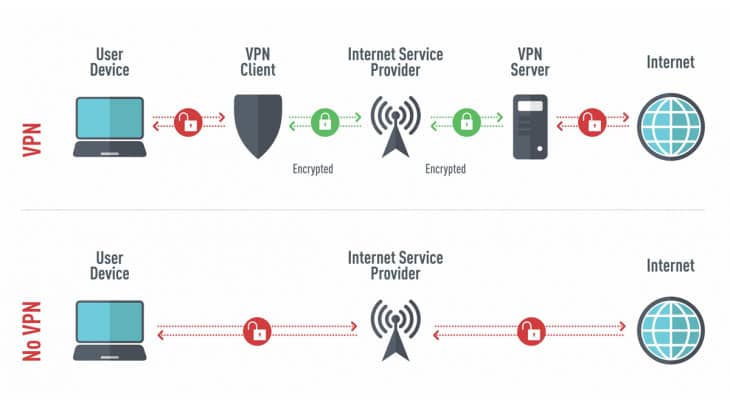
Wire, Guard is much faster than Open, VPN. It takes in 15% less data, manages network modifications better, and seems safe and secure. Nevertheless, Open, VPN has been tried and tested, is more privacy-friendly, and is supported by a bigger variety of VPNs.
What Is Wireguard? (Full Guide)
We might get payment from the products and services mentioned in this story, however the opinions are the author's own. Payment might impact where deals appear. We have not consisted of all readily available products or offers. Find out more about how we generate income and our editorial policies. Today, virtual personal networks (VPNs) have removed, getting appeal with those searching for additional security, personal privacy, and flexibility.
In this short article Wire, Guard is a new, open-source VPN procedure developed with cutting edge cryptography, which is the practice of coding delicate info so just the designated receivers can translate its meaning. It offers quicker, easier-to-use, and more protected pathways for user gadgets to get in touch with VPN servers worldwide. Designer Jason A.
Dealing With Wire, Guard could not be simpler. Users start by finding the Wire, Guard application in an online shop, then follow simple download and setup actions. The Wire, Guard app is readily available for desktop and mobile phones for included convenience. Wire, Guard keeps it basic by running with less than 4,000 lines of code compared to older VPN procedures that usually utilize thousands more.
Latest Posts
The Best Vpns For Small Business In 2023
Best Vpns Of 2023
5 Best Vpns For Mobile Data To Protect Your Privacy